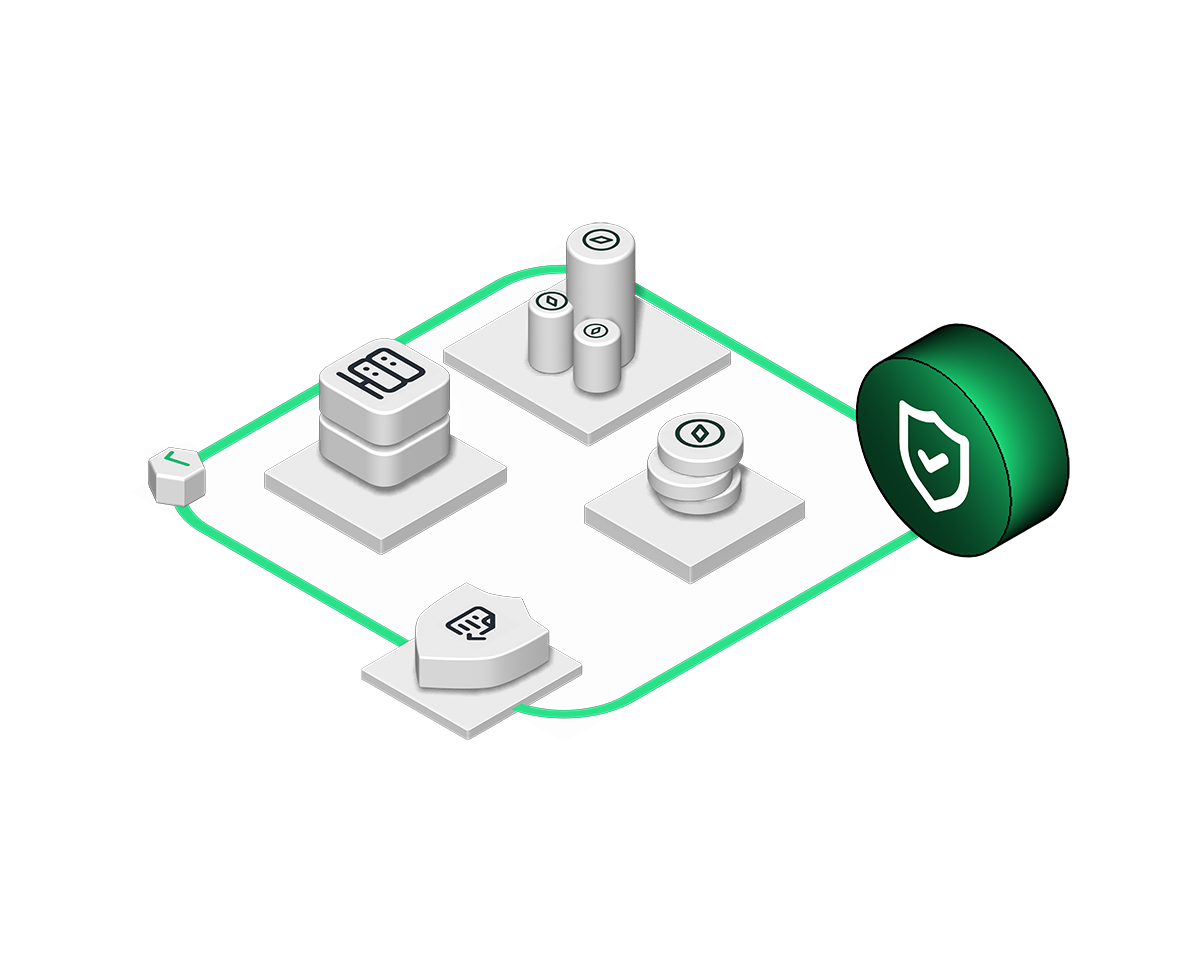
Our Architecture
Hover your mouse over the diagram for more information
Sending A Transaction Flow
This is the process for outbound transactons
Stage 1
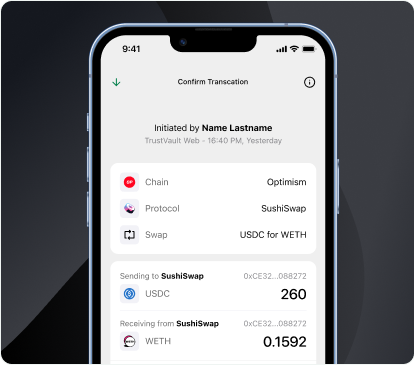
Customer initiates a transaction instruction either in TrustVault Web, the mobile app or MetaMask. TrustVault will then request signatures from the signers on the wallet policy.
Stage 2
TrustVault will evaluate any rules that are specified on a customer’s wallet. This can be various rules like max threshold rules, or that the address is in an Allow List.
Stage 3
Our automated compliance process checks the transaction using our integration with Chainalysis.
Stage 4
When the transaction instruction has a fully satisfied policy (i.e. the right number of signers have signed) it is sent to TrustVault’s Hardware Security Module (HSM) where it is signed with the private key.
Stage 5
Once signed with the private key the transaction is submitted to the blockchain or, if required, simply returned to the customer.
How A Transaction Arrives
This is the process for inbound transactions
Stage 1
A third-party initiates a transaction to the customers' public wallet address.
Stage 2
The transaction is received and KYT checks are applied to the incoming funds using our Chainalysis integration.
Stage 3
Any customer notifications (iOS push or webhooks) are sent with the transaction details.
Stage 4
The assets are now secured and ready to be deployed elsewhere if wanted.


ISO/IEC 27001:2013
- Security:ISO/IEC 27001:2013 certification assures your digital assets are stored securely. The company implements stringent security protocols so as to protect your investment against unauthorized access and malicious attacks.
- Data Protection: All customer data is securely stored and continuously monitored under ISO/IEC 27001:2013 standards. Your personal information, such as contact details, financial information and trade data, is kept confidential and protected.
- Compliance: Our ISO/IEC 27001:2013 certification provides assurance that our custodial services and infrastructure are regularly inspected and comply with industry regulations.


We received a SOC 2® report from A-LIGN, an independent CPA firm
- Enhanced Security Assurance: Our SOC 2 assessment provides you with the assurance that our security controls are designed effectively to protect your digital assets. This demonstrates our commitment to safeguarding your investments and data, reassuring you that we have the necessary safeguards in place.
- Streamlined Due Diligence: As a SOC 2 assessed custodian, we simplify your due diligence process. You can confidently partner with us, knowing that we have undergone a rigorous independent assessment of our control environment. This reduces your efforts in assessing our security and compliance practices, making it easier for you to make informed decisions.
- Reduced Risk: By choosing a custodian that's been SOC 2 assessed, you reduce your exposure to security risks and potential breaches. Our assessment signifies that we have proactively addressed security vulnerabilities, decreasing the likelihood of incidents that could impact your assets. Your investments are safer with us.
Stay in the loop
Stay up-to-date with the latest in the crypto industry and Bitpanda Custody. Be in the know, sign up today